#Secure Android spy app
Explore tagged Tumblr posts
Text
ONEMONITAR: India's Top Android Spy App

Discover the power of ONEMONITAR, a leading Android spy app and one of the best phone monitoring solutions in India. With advanced tracking features, real-time updates, and user-friendly controls, ONEMONITAR ensures you stay informed about your loved ones' digital activities.
Perfect for parents and employers, this trending app provides comprehensive insights into call logs, messages, GPS locations, social media interactions, and much more. Trust ONEMONITAR for reliable, discreet, and efficient phone monitoring.
Try ONEMONITAR today and stay connected, stay secure!
#Android spy app#Best Android spy app#Android spy app India#Top Android spy app#Hidden Android spy app#Android spy app download#Android spy app for parents#Android spy app for employers#Android spy app with GPS tracking#Secure Android spy app
0 notes
Text
PSA for anyone with an Android phone. Delete your Meta apps (Facebook, Facebook Messenger, Instagram, WhatsApp, Threads). They are spying on you. Much worse than you thought they were. (June 7, 2025)
Gift link to a Washington Post article: https://wapo.st/45hNMeB
Quote from the article:
…apps from Meta and Yandex, a technology company that originated in Russia, circumvented privacy protections in Android devices in ways that allowed their apps to secretly track people as they browsed the web.
That should not have happened. Apps on your phone are walled off from accessing your activity on other apps, including web browser apps like Chrome. Meta and Yandex found work-arounds.
The techniques essentially were akin to malware, or malicious software that is surreptitiously planted on your phone or computer, Dolanjski said.
Google said the behaviors of Meta and Yandex “blatantly violate our security and privacy principles.”
Technical analysis from Ars Technica: https://arstechnica.com/security/2025/06/meta-and-yandex-are-de-anonymizing-android-users-web-browsing-identifiers/
Note: the WaPo article says that so far, there’s no evidence this is happening on iPhones, but that it would be theoretically possible. So you should probably delete your Meta apps on iPhone, too.
50 notes
·
View notes
Text
Object permanence

I'm on a 20+ city book tour for my new novel PICKS AND SHOVELS. Catch me in PDX on Jun 20 at BARNES AND NOBLE with BUNNIE HUANG. After that, it's LONDON (Jul 1) and MANCHESTER (Jul 2).

#15yrsago InfoLadies of Bangladesh revolutionize rural life https://www.theguardian.com/journalismcompetition/professional-two-wheel-triumph
#15yrsago Google and Viacom blend high-profile copyright suits with extreme profanity, as nature intended https://arstechnica.com/tech-policy/2010/05/f-those-mother-f-ers-youtubeviacom-lawsuit-gets-dirty/
#15yrsago Google offers encrypted search https://www.eff.org/deeplinks/2010/05/google-launches-encrypted-search
#15yrsago The Boneshaker: magic, latter-day Bradburian novel for young adults https://memex.craphound.com/2010/05/21/the-boneshaker-magic-latter-day-bradburian-novel-for-young-adults/
#15yrsago Scientology raid uncovers dossiers on local “enemies”: sexual habits, health info, political opinions https://www.ansa.it/web/notizie/rubriche/english/2010/05/20/visualizza_new.html_1794804082.html
#15yrsago Cracked vs. RIAA damages https://web.archive.org/web/20100524024915/http://www.cracked.com/funny-4003-the-pirate-bay/
#10yrsago NSA wanted to hack the Android store https://www.cbc.ca/news/canada/spy-agencies-target-mobile-phones-app-stores-to-implant-spyware-1.3076546
#10yrsago GM says you don’t own your car, you just license it https://web.archive.org/web/20150522003554/https://consumerist.com/2015/05/20/gm-that-car-you-bought-were-really-the-ones-who-own-it/
#10yrsago Today’s terrifying Web security vulnerability, courtesy of the 1990s crypto wars https://memex.craphound.com/2015/05/21/todays-terrifying-web-security-vulnerability-courtesy-of-the-1990s-crypto-wars/
#10yrsago Mark Zuckerberg just dropped another $100M to protect his privacy https://slate.com/business/2015/05/tech-billionaires-and-privacy-why-facebook-s-mark-zuckerberg-is-spending-millions-on-a-private-island.html
#5yrsago How spy agencies targeted Snowden journalists https://pluralistic.net/2020/05/21/profitable-butchers/#sources-and-methods
#5yrsago Monopolies killed corporate R&D https://pluralistic.net/2020/05/21/profitable-butchers/#all-d
#5yrsago Spotify's trying to kill podcasting https://pluralistic.net/2020/05/21/profitable-butchers/#rogan-monopolist
#5yrsago Black Americans' covid mortality is 2.5X white mortality https://pluralistic.net/2020/05/21/profitable-butchers/#ethnic-cleansing
#5yrsago On Madame Leota's side-table https://pluralistic.net/2020/05/21/profitable-butchers/#details-details
#5yrsago Private equity's healthcare playbook is terrifying https://pluralistic.net/2020/05/21/profitable-butchers/#looted
#5yrsago Patent troll sues ventilator makers https://pluralistic.net/2020/05/21/profitable-butchers/#ip-edge
#5yrsago The Lost Cause and MMT https://pluralistic.net/2020/05/21/profitable-butchers/#byebye-falc
#5yrsago Walt's grandson calls for Disney execs' bonuses to be canceled https://pluralistic.net/2020/05/21/profitable-butchers/#brad-lund
#1yrago Linkrot https://pluralistic.net/2024/05/21/noway-back-machine/#pew-pew-pew

6 notes
·
View notes
Text
Cell-site simulators mimic cell towers to intercept communications, indiscriminately collecting sensitive data such as call metadata, location information, and app traffic from all phones within their range. Their use has drawn widespread criticism from privacy advocates and activists, who argue that such technology can be exploited to covertly monitor protestors and suppress dissent.
The DNC convened amid widespread protests over Israel’s assault on Gaza. While credentialed influencers attended exclusive yacht parties and VIP events, thousands of demonstrators faced a heavy law enforcement presence, including officers from the US Capitol Police, Secret Service, Homeland Security Investigations, local sheriff’s offices, and Chicago police.
Concerns over potential surveillance prompted WIRED to conduct a first-of-its-kind wireless survey to investigate whether cell-site simulators were being deployed. Reporters, equipped with two rooted Android phones and Wi-Fi hotspots running detection software, used Rayhunter—a tool developed by the EFF [Electronic Frontier Foundation] to detect data anomalies associated with these devices. WIRED’s reporters monitored signals at protests and event locations across Chicago, collecting extensive data during the political convention.
...According to the EFF’s analysis, on August 18—the day before the convention officially began—a device carried by WIRED reporters en route a hotel housing Democratic delegates from states in the US Midwest abruptly switched to a new tower. That tower asked for the device’s IMSI and then immediately disconnected—a sequence consistent with the operation of a cell-site simulator.
“This is extremely suspicious behavior that normal towers do not exhibit,” Quintin [a senior technologist at the EFF] says. He notes that the EFF typically observed similar patterns only during simulated and controlled attacks. “This is not 100 percent incontrovertible truth, but it’s strong evidence suggesting a cell-site simulator was deployed. We don’t know who was responsible—it could have been the US government, foreign actors, or another entity.”
3 notes
·
View notes
Text
new phone going well so far. I'd forgotten how much of a faff it is to get everything to work
1 - When you're using 2FA: you need a code sent by email but you haven't set up that email yet. You need the code to set up the thing that'll get you into your emails. No, you're not getting my mobile number, thankfully the old phone works while kept charged.
2 - 12 different security alerts + 24 notifications because you used a different phone to use some app that has access to nothing important.
3 - Removing google. tentacle sucker by tentacle sucker in 4 different places. Oh hey what's this left swipe to my phone home screen?! no I don't want the news by google, what even is its name to disable it?
4 - Incremental updates. the OS has changed a few times since late 2017 but we're going to download the full 1.5GB for half hour then pretend we're up-to-date, then repeat. Thank goodness i'm on Wi-Fi, slow Wi-Fi but still - my mobile plan only has 100MB a month.
5 - We said we synched/cloned your preferences but that was a lie: firefox (no adblock, new sponsors on the homepage), swiftkey (different languages, layouts, font size, privacy settings reset), anything google related.
oh well at least it's ten times easier than trying to disable the spying on a smart TV.
but for a moment there after I'd cloned my hard drive (remember how windows said that was a bad idea and it turned out fine?) I forgot you can't just clone a phone.
I intend to make this beautiful little thing work For Me so on we go to probably hour 8 now, of multitasking while it does it little updates and I roll back whatever privacy settings got reverted and remove bloatware. I could of course flash the thing but it'd take that much time in research and being sure I'm not bricking a nice working phone. not ready at this point.
// This is not helped by the nerd infighting on which stripped android os is better.
I don't mind the stupid usernames I ran win7 super unfucked haxxor edition by touhouhusbando or whatever for a few years but seriously, researching is like "here is the one, the real deal, the bestest": three notes down "btw I'll have headphones working in a month or so - sent in 2022" //
Update 7, we're now upto 2020 the last couple have been 4gb. I should have probably rooted my phone and flashed darkjoker's super android stripped extreme (or whatever). OTL
4 notes
·
View notes
Text
Can a spy app be installed remotely?

The rise of the internet has surely made the world a smaller and better place. The advancement of technology to such an extent that you just have to make a few clicks to get anything was unimaginable a decade back. A huge spike in the number of internet users has been seen in just the past few years. If you look around, you can find everyone with their smartphones in their hands, engaged in some sort of content. Apart from the ability to stay connected with people, it has enabled us to run a whole business just through a smartphone.
However, like any good thing in life, this also came at a cost of being exposed to various online risks. Fortunately, these risks are totally avoidable with the use of a mobile spy app like Chyldmonitor. The app lets you monitor the online activities of your family and friends to keep them safe over the web. Not everyone out there can be educated about the risks involved and how not to fall for it. The whole process of creating awareness around the hazards of the internet is neither realistic nor doable. Therefore, using an spy app for android is the best solution one can opt for.
Making yourself aware of the risks and how to deal with them, can really help your loved ones to browse safely. However, the biggest question that people get when it comes to spy apps is whether they can be remotely installed or not.
The answer is no. But the good news is that you need access to their phone for about 5 - 7 minutes only for the whole process to complete. This should be very doable for anyone who wants to spy on someone for their sake. You can ask to use the targeted phone for a while, and before they know it, you’ll be able to set up the whole thing.
Beneficial Features Provided by the Chyldmonitor App
The app is offering more than 60+ features to their users all over the world. With this app in your toolbag, you get to fully monitor the target phone. Not a single aspect which could prove to be harmful for your family is spared by the app. The app comes packed with features like call recordings, location tracking, access to chats, ambience sound recording, etc.
The app also has a hidden call recorder feature available to record every call taking place on the targeted phone. With its unique feature of remaining hidden from the app drawer, there’s no way anyone can know if they’re being spied on.
Apart from this, one also gets the option to track location of the intended device. Majority of the scams these days are taking place over the most used communication platforms. This is where WhatsApp Spy feature can help you to maintain the security of your loved ones. Frem the recordings of the calls made over WhatsApp, to the media shared, everything can be accessed from the web portal once you login to your account.
Install a Spy App in Your Phone This Easily
Many people think that installing a spyware application on the intended device must be a complicated process. The word ‘rooting’ or ‘jailbreaking’ comes to their mind when they think about it. However, with Chyldmonitor application, you are not required to root your device to get advanced permissions. The app is fully functional on any android device.
Once you have managed to get a hold of the targeted device, the installation process will only take you about 7 minutes at most. If you face any trouble while installing the app, their customer service is available 24x7.
You can be guided through the installation process over the call or the agent might take remote access to your device, to perform the installation on your behalf. It has gotten way easier than ever to spy on your family and friends to keep them protected over the internet. However, no ethical boundaries should be crossed in the process. The consent is the crucial thing to make sure that your relationship doesn’t get affected with the intended person on whom you want to spy on.
The arrival of spy apps have revolutionized the way in which we deal with the online threats. Monitoring the online activities of your loved ones is the only reasonable way today to ensure their safety online.
#androidspy#mobilespy#spyappformobile#hiddencallrecorder#spyapp#spyappforandroid#androidspyapp#parentalcontrol#phonespy#whatsappspy#whatsappspyapp
2 notes
·
View notes
Text
How to Know If Your Cell Phone Has Been Hacked?

What are the significant signs that are used to find out that someone’s phone has been hacked and its information stolen by other people? This question and all similar questions are the common concern of many smartphone users, and considering that the phone is a versatile tool for most people, important information is also stored in it, so hacking the phone and stealing it Losing its information can cause a lot of damage. In order to know whether your smartphone is being spied on or not, follow this article and the security solutions mentioned here.
2 signs that someone is spying on your phone
There are lots of important physical and hardware signs that show your phone is being hacked. In order to find out, continue with us in this part of the article.
You are receiving unusual messages
If you receive unrelated and incomprehensible messages that have never happened before, for example, messages that contain a large number of characters and numbers, you are probably under control. These messages are similar to the codes that are sent to track the location of people.
AnyControl is the best phone call monitoring app that can track every incoming, outgoing and missed phone call on the target device even if the call log is deleted with its advanced tracking features.
Another way that can reveal the signs of espionage from a software point of view are anti-spyware programs and apps. An example of these apps is Anti Spy Mobile. iPhone phones are usually more secure than Android phones (if they are not jailbroken or unlocked), so if your phone is an iPhone, you can be sure of its greater safety; Because installing spyware requires physical contact with the device.
After sending, a lot of information will be displayed. Pay more attention to URLs. If you have been spied on, many copies of the email you have sent will be sent to different IPs that are different from the IP of your Internet service provider. You can search the term IP lookup on the Internet to distinguish the IP of your ISP from other IPs.
Your data usage has been checked by phone
Through smartphones, you can check the internet usage under the phone's network usage. The spy softwares that is installed in the devices for spying perform their activities by sending and receiving data, which is actually the same as using the Internet. If you see significant changes in your phone's internet usage, there is a possibility that your device is being tapped and its information is being spied on.
2 notes
·
View notes
Text
Today, as the smart phone has become the device of choice for all those on the move for accessing the Internet, data security has become an extremely sensitive issue the world over. Malware, viruses amongst other threatening software rule the dark side of the Internet with impunity. Extreme levels of care need to be taken, especially when the driving engine behind most smart phones is the Android OS. As Android comes in many flavors as of today, and since it has been adopted by the majority of handset manufacturers globally, this issue has required to be tackled on a priority basis and on a war footing. The scenario can be even worse, if your phone is stolen or is accessed by undesired people. This article examines best apps for Smart phone security, especially those which are running Android: iPhone owners may want to checkout our list of security apps for iOS devices. Lookout If you are on the lookout for a free mobile app that is capable of protecting your android device around the clock from a wide range of mobile threats then Lookout Mobile Security is the right answer for you. This app is the perfect device security system in the post PC era. Lookout can secure you from unsecure WiFi networks, fraudulent links, malicious apps, etc. Lookout Mobile Security can also backup contacts such as scheduling automatic backups, which can later be accessed online. It can also use this information to restore your device in case your phone crashes, or in the event of a data loss. You can also locate your phone on a Google map in case your phone is lost, even if the GPS is off. Most of the top features are available for free with this app. However, the premium version offers much more with features such as remote locking, privacy scans, safe browsing, phishing protection, and app reports. Anti Spy and Spyware Scanner This app is a good help to identify any spyware apps on your android device. This can help you find and remove any spyware or location trackers that you do not see in list of installed apps. Avast Free Mobile Security This is a free mobile security app from the popular antivirus developer Avast. The Avast Free Mobile Security App includes a wide spectrum of anti malware as well as anti-theft features. Also included is browsing protection. This prompts the user if s/he visits a malicious website. Users can also make good use of the privacy advisor, which helps you identify potentially dangerous installed apps. At the same time, an application manager lets you manage running apps. Avast Free Mobile Security also includes SMS and call filtering. This feature helps block incoming messages as well as calls including outgoing calls that are based on times and contacts selected by the user. While the app lacks any backup functionality, enhanced anti-theft features along with a firewall are provided for rooted devices. With Avast, it is also possible to automatically scan apps that you install. Avast can also do full scans of your installed apps on the phone and on the SD card. This can be done manually or you can even specify the days and times for automatic scans. ESET Mobile Security & Antivirus The ESET mobile security comes with an interface that is completely easy to use as it provides real-time scanning of apps to detect malware and devious apps that try to send texts or make premium rate calls. The ESET mobile security basic version is completely free and it also includes a set of anti-theft tools. With ESET Mobile Security and Antivirus, it is also possible to remotely locate as well as lock your Smartphone or tablet. This feature also prevents anyone from uninstalling apps, by providing password protection. However, the remote wipe or SIM guard capabilities are available only with the premium version, which you have to pay for. This version provides additional features such as anti-phishing protection, an app audit feature, device monitoring so that unnecessary use of data can be checked, as also advanced call blocking.
Avira Antivirus Security The Avira Antivirus Security for Android phones provides 100% detection rate along with no false positives. Hence, users can trust the free version of Avira to keep their android Smartphone or tablet safe. At the same time, it has a light footprint when it comes to performance. Also, it has a minimalist as well as sleek design, so that it fits snuggly with the Android platform. With Avira, it is possible to scan apps for potential trouble, and it scans new apps or updates automatically. Also provided are a set of anti-theft tools, so that you can find your device remotely, or perform other actions such as locking, wiping, or even triggering an alarm. Avira also provides an additional tool, which it claims is able to tell you whether your email account has been hacked, and what action you need to take if you have to. Also included are a variety of blacklisting options that can potentially take care of nuisance callers and spam. BullGuard Mobile Security BullGuard Mobile Security is a premier quality mobile security app that provides you with an online account so that you can remotely access your smart phone. You are also provided with a mobile security manager that works in tandem with your GPS, so in the case you lose your device, it can be easily locked remotely and can be wiped clean. The BullGuard Mobile Security also includes a parental control module. This allows you to keep your children protected without directly accessing the phone. The app also includes anti-virus and anti-spyware, firewall, spam-filter, backup and restore features for contacts, along with SIM card protection. This app is available for Android, Symbian OS, Windows mobile, and Blackberry phones. 360 Mobile Security With a detection rate of 100%, the focus of 360 Mobile Security (developed by Chinese Player Quiho) is a lightweight, streamlined and elegantly designed app that is completely free. With 360 Mobile Security, it is possible to safeguard your device from malware, spyware, and any threats of infection. At the same time, it is also capable of detecting as well as fixing system vulnerabilities. 360 Mobile Security cleans up idle background apps so that it can help your phone run more efficiently. The app also includes a privacy advisor so that you can clear your usage history. In favor of a light touch, the app does not include a long list of extras. So, you will only find additional features such as call blocking, short cut toggles, as well as safe browsing option. This app also excludes the anti-theft component or the backup option. Android Device Manager This is a must have app for all its useful features. With the ability to track your lost device, and even ring it at max volume if you cannot find it, you couldn’t’ find a better app elsewhere. You can even lock your device or wipe your device from the web interface. This is a good way you can keep all sensitive data out of the hands of others. The best part of the deal is that this device is free. Hotspot Shield VPN This is a VPN app for your android device and is one of the most reasonably priced as well as popular VPN apps for android. With HotSpot VPN, can detect unsecured Wi-Fi to automatically enable HTTPS protection as well as automatically unblock content whenever certain apps or sites are accessed. It encrypts traffic in and out of your device for ultimate privacy. The Wi-Fi connection is secured with banking level HTTPS encryption, as your Wi-Fi network can be vulnerable even if the device is secure. It prevents hackers from stealing your private information and mask your IP address to browse the web anonymously as well as privately. Snap Secure Snap secure can automatically back up your data to your online account on a secure basis. From here, you can easily access your data, restore it, or transfer it to a new device if necessary. Snap Secure comes along with anti-virus as well as anti-spyware protection. It can also scan your new applications for malware.
Calls from unknown or un-shown numbers and also unwanted SMS messages on Android devices can be easily blocked. Snap Secure also includes a much-wanted privacy manager, in order to help you understand how apps are using your personal information. Also included are an anti-theft and a location tracker, which can be utilized in the case of the theft of your mobile device. Another unique feature called the Personal Guardian helps the user to press a panic button to send out an email, SMS, or tweet along with your location, in case the user is in the midst of an emergency situation. This app is also available for iOS and BlackBerry devices. Both free as well as pro versions are available. You may also be interested in VPN server software for other devices. Cerberus Anti Theft This is a free anti-theft app that includes many features which you can use for finding your lost or stolen device. With a standard web interface that you can see your device’s location, you can lock the device; hide the app from the app drawer, so that people will not know it exists. You can even record audio from the microphone to know what is going on around it as well as get information about the service the phone is connected to while getting call logs as well. You can even remote control your phone through their website and even via text messages. At the same time, you can even obtain alerts via the SIM checker if someone uses the phone with an unauthorized SIM card. Shivani Ajmerani works for Fusion Informatics Ltd., a mobile applications development company that also offers Custom android application development services. She loves leveraging the immense potential of the Internet to achieve corporate goals. Jennifer Brown is working as a software developer into the IT Company Digital Infoware Pvt. Ltd. since the last 3 years. I enjoy writing articles as a hobby on topics related to software, mobile app development, tutorials etc.
0 notes
Text
Price: [price_with_discount] (as of [price_update_date] - Details) [ad_1] MSTECH HD 1080P Video live view & 120° Wide Angle Lens: With 120 degree wide angle lens, the mini spy camera allows you to see more details happening in the room. The quality lens also features 1080P video and pictures that perfect surveillance camera for your Office or business place. 24/7 Home Security in Your Hands: Whenever you're using a smartphone/ tablet/ computer device, you can view the HD live streaming by HD PLUS hidden cameras. Multi-User & Multi-View: One camera can support multiple users and one app can support multiple cameras simultaneous so you can check up on your property in real-time. Compatible with iOS, Android, Mac and Windows devices. Multi Use: You can put this mini camera in your home, office, warehouse, store, garden. It can also be used as a car camcorder, aerial action camera, pet camera, cop camera. Specifications: Function: Support WiFi, Video, Camera, Loop Recording, Motion Detection, Infrared Night Vision, Time Display. Resolution: 1080P/720P Video Format: AVI Picture Format: JPEG Frame Number: 30fps Visual Angle: 120 degree Recording Range: 5 m2 Compressed Format: H.264 Recording Time: Over 1 hour Charging Time: 1.5 hours Voltage input: DC 5V 1A Interface: MICRO USB Interface Package Includes: 1x Mini Camera 1x Bracket 1x Iron Sheets 1x USB Charging Cables 1x Mini USB Charging Cable 1x Instruction. Batteries : 1 Lithium Polymer batteries required. (included) Product Dimensions : 3 x 2 x 2 cm; 25 g Date First Available : 31 March 2023 Manufacturer : MSTECH ASIN : B0C14PB681 Item model number : MS-WIFI-Magnet-Camera Country of Origin : China Manufacturer : MSTECH, MSTECH Packer : MSTECH Importer : MSTECH Item Weight : 25 g Item Dimensions LxWxH : 30 x 20 x 20 Millimeters Net Quantity : 1.00 count Included Components : 1x Mini Camera 1x USB Charging Cables 1x Generic Name
: Hd Wifi Camera MSTECH : As A mini WIFI Camera, It built-in 250mah battery, fully charged, can work about 1 Hours , Also you can get the camera plugged into a USB charger (or power bank) for recording 24/7 hours. With Wifi connectivity to room's 2.4GHz router, you can watch live video feed or playbacks no matter where you are by accessing the APP. MSTECH : The wireless hidden camera will send push notification with images to your phone once motion is detected. You can log into the App to see what’s going on in real time and never worry about missing something important. This hidden spy cam automatically records and overwrites the oldest SD card files when full for continuous recording. MSTECH : One camera can support multiple users and one app can support multiple cameras simultaneously. This spy camera features hotspots so it can record without Wi-Fi too: just insert a SD card (not included) and turn on, the mini WiFi camera will auto record HD video files to sd card; It can also record videos even if the network is offline. MSTECH : Built-in 6 infrared lights for a clear display in low light condition(No-Glow in use), the light working distance reach to 5m which makes it perfect as a home security camera or a housekeeper/ nanny cam for recording both snapshot picture and videos without attracting any attention. With the internal magnet, Upgraded hidden camera can be adsorbed on any iron surfaces easily. MSTECH : HD plus small mini cam records video in exceptional 1920X1080P HD at 30 frames per second. Function with video, picture, loop recording, motion detective, infrared night vision, time display, magnetic, etc.120° wide angle view that can monitor anywhere in standard distance. Battery Backup After Full Charger 50 to 60 Minutes [ad_2]
0 notes
Text
Can You Track IMEI Number Through Google Earth? (Spoiler: No, But Here's What Works)
Can You Track IMEI Number Through Google Earth?
Okay, so your phone's gone. Maybe lost. Maybe stolen. And now you're googling like crazy trying to find it.
Someone told you about tracking IMEI numbers with Google Earth? Yeah, I've been there too. Spent hours trying to make it work.
Bad news first. It doesn't work. At all.
But don't worry. I'll show you what actually does work. And save you from the same mistakes I made.
First Thing: What's an IMEI Number Anyway?
IMEI is just a fancy name for your phone's ID number. Every phone has one. No two are the same.
It's like your phone's social security number. Except it's 15 digits long.
Here's what mine looks like: 352094087654321.
Want to find yours? Easy:
Type *#06# on your phone
Check your phone settings
Look at your phone's box
Check under your battery (if you can remove it)
When I first heard about IMEI, I thought it was some spy stuff. Nope. Just a boring number that identifies your phone.
Can Google Earth Track Your IMEI? Nope.
Let me save you some time. Google Earth cannot track IMEI numbers.
I know. Bummer, right?
It sounds like it should work. Google Earth has all those satelite photos. Your phone has a unique number. Put them together and... nothing.
Because that's not how it works.
Here's Why It's Impossible
Google Earth is just photos. That's it. Pictures taken from space.
Think about it. Can you see your phone from space? No way.
Even if you could, how would Google Earth know it's YOUR phone? It can't read IMEI numbers from orbit. That's science fiction stuff.
I wasted three hours trying every "trick" online. Nothing worked. Because physics doesn't work that way.
It's like trying to use binoculars to hear someone's conversation. Wrong tool, wrong job.
So How Does Real IMEI Tracking Work?
Actual IMEI tracking is totaly different. And regular people can't do it.
Only these folks can track IMEI:
Your phone company (Verizon, AT&T, etc.)
The police
Sometimes the phone maker
Here's the deal. Your phone talks to cell towers. When it does, it shares its IMEI. The phone company logs this.
But catch this. Your phone must be:
Turned on
Have a SIM card
Connected to a network
Phone turned off? Can't track it. SIM card removed? Forget about it.
Those "Track Any IMEI" Websites Are Scams
Trust me on this one. Every single website that promises IMEI tracking? Fake. All of them.
I tested dozens. Here's their playbook:
You type in your IMEI
They show a fancy "scanning" animation
They ask for money
You pay (don't do this!)
They give you nothing
Some are nastier. They might:
Put viruses on your computer
Steal your info
Use your IMEI for bad stuff
Almost fell for one myself. My bank saved me by blocking the payment. Thank god.
What to Actually Do When Your Phone Goes Missing
Forget Google Earth. Here's what works:
1. Use Your Phone's Built-In Tracking
Got an Android?
Go to android.com/find
Log in with your Google account
Pick your phone
See where it is (if it's on)
Got an iPhone?
Go to iCloud.com/find
Log in with your Apple ID
Click your phone
Check the map
I've used both. They work great. But only if your phone's on and online.
2. Call Your Phone Company NOW
Don't wait. Call them immediately. Tell them what happened. Give them your IMEI.
They can:
Block your phone
Stop anyone from using it
Sometimes show where it last connected
Once they blacklist your IMEI, that phone becomes a paperweight. Good.
3. Get a Police Report
I know, I know. Cops probably won't launch a manhunt for your phone. But you need that report.
Why? Insurance claims. Plus, sometimes cops find batches of stolen phones. They use IMEI numbers to return them.
Happens more than you'd think.
4. Change All Your Passwords
Super important. People always forget this part.
Change passwords for:
Email
Banking apps
Social media
Any app with your credit card
Do it now. Not later. Now.
Myths That Drive Me Crazy
Let's kill some myths:
"Anyone can track IMEI numbers" Nope. Only phone companies and cops. With the right tools.
"Secret apps can track any IMEI" These are scams. Or viruses. Usually both.
"Google Earth has hidden IMEI features" It doesn't. Google Earth shows maps. That's all.
"Hackers track IMEI easily" Actually pretty hard. They'd need to hack your phone company.
About Those YouTube Videos...
Oh man. Those videos make me mad.
"Track ANY Phone with Google Earth!" Millions of views. All fake.
They show:
Fancy computer screens
Random typing
Fake "hacking"
Magic phone finding
It's all video editing. Hollywood tricks. Total BS.
I tried copying one once. Wasted an hour. Felt real dumb after.
Is IMEI Tracking Even Legal?
Quick reality check. Even if you COULD track someone's IMEI (you can't), it's probably illegal.
Tracking people without permission is:
Creepy
Illegal
Called stalking
Only legal reasons to track:
Your own lost phone
Your kid's phone (if they're underage)
Company phones (that the company owns)
Cops with warrants
Don't track your ex. Or your neighbor. Or anyone. Just don't.
Stuff That Actually Works
Stop chasing IMEI fantasies. Try these instead:
GPS Apps That Work
Like:
Life360
Find My Friends
Google Maps sharing
These work. But everyone has to agree to share location.
Bluetooth Trackers
Those AirTag things? Or Tiles? They're great.
Not for phones exactly. But amazing for keys and wallets. I got one after losing my keys a million times. Best 25 bucks ever.
Security Cameras
Worried about theft? Cameras beat any tracking. They might not find your stolen phone. But they stop theft before it happens.
My Phone Got Stolen. Here's What Happened.
True story. Coffee shop. Put my phone down. Looked away for five seconds. Gone.
First thought? "I'll use the IMEI to track it!"
Yeah, right.
What actually worked:
Opened Find My iPhone on my laptop
Saw it moving away fast
Called cops with the location
Locked it remotely
Put my number on the screen
Thief dumped it once it locked. Good person found it. Called me. Got it back next day.
Never used the IMEI once.
Why Do People Fall for This?
Good question. Why do smart people think Google Earth tracks IMEI?
My theory:
Both sound high-tech and mysterious
Movies show impossible tracking
Desperate people try anything
Scammers keep lying about it
Like those Nigerian prince emails. Obviously fake. But desperation makes people stupid.
Will This Ever Be Possible?
Will satelites ever track IMEI numbers?
No.
Satelites take pictures. They don't read electronic signals from phones. Two different things entirely.
What might get better:
Phone tracking features
Faster police response
Better security systems
More phones recovered
But Google Earth reading IMEI? Never gonna happen.
Keep Your Phone Safe (So You Don't Need Tracking)
Better to not lose it in the first place, right?
Keep It Physically Safe
Never leave it alone
Front pockets, not back
Watch it in crowds
Get a case with a strap
Digital Safety Too
Use a real passcode (not 0000)
Set up fingerprint lock
Turn on find my phone
Back up everything
Just In Case
Write your IMEI somewhere
Photo your serial number
Save your carrier's number
Maybe get insurance
This boring stuff works better than satelite tracking dreams.
Simple Tips Everyone Ignores
The best advice is usually the most obvious.
Don't:
Wave your expensive phone around
Leave it on tables
Let strangers "borrow" it
Skip security updates
I learned all this the hard way. Several times. I'm not that bright aparently.
Here's the Deal
Lost phones suck. Stolen phones are worse.
But Google Earth won't help. Can't track IMEI. Never could. Never will.
What works:
Find My Phone features
Calling your carrier fast
Police reports
Being careful
What doesn't:
Fake tracking websites
Bogus YouTube videos
Scam apps
Google Earth dreams
Stick with what works. Skip the fantasy.
My Final Take
I've wasted so much time on this. Testing everything. Trying every method.
Know what I learned? Boring security beats exciting myths.
Strong passwords. Regular backups. Being careful. Not as cool as satelite tracking. But it works.
So when someone says they can track IMEI with Google Earth? Now you know better. Send them this article. Save them the headache.
Lost your phone? Skip Google Earth. Use Find My Device. Call your carrier. File that report.
Yeah, it's boring. But boring works.
Keep your phones safe, friends. The smart way. Not the Google Earth way.
Quick note: This is just for learning. Respect privacy. Only track your own stuff. And seriously, those YouTube videos are fake. All of them.
0 notes
Text
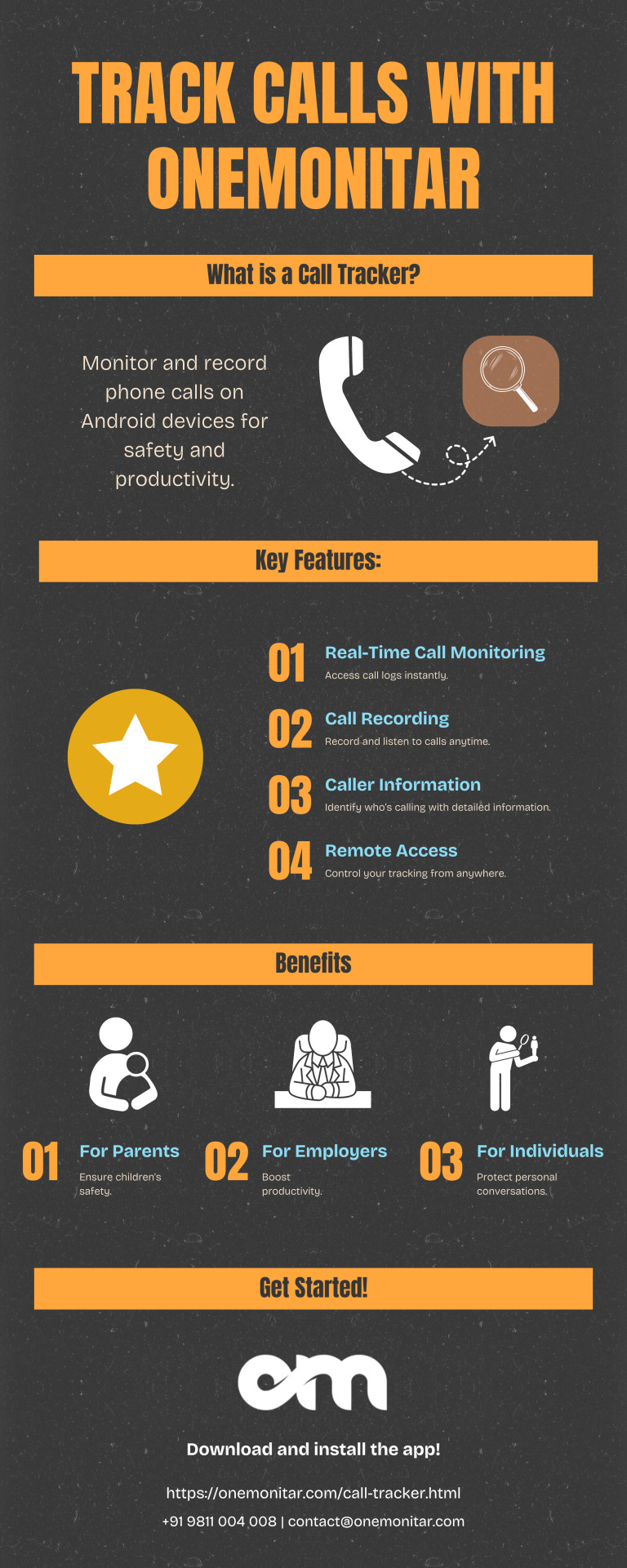
Discover the power of ONEMONITAR’s Call Tracker! Monitor and record phone calls on Android devices with real-time tracking, call recording, and caller details, all from anywhere. Whether you’re a parent ensuring your child’s safety, an employer boosting productivity, or an individual protecting your conversations, ONEMONITAR is your go-to solution. Easy to use, secure, and backed by 24/7 support—get started today!
#Call tracker#Phone call monitoring#Call recording app#Android call tracker#Real-time call monitoring#Remote call access#Call spy app#Phone spy software#Parental control app#Employee monitoring app#Secure call tracker#Phone tracking app#ONEMONITAR call tracker#Monitor phone calls#Call tracker for Android
0 notes
Text
WhatsApp Spy Features for Child Safety

Going that extra mile and protecting your children is top-most priority for every parent. With great exposure to smartphones and technology, there is an obvious feeling of concern for parents to know what their child is up to.
With the help of a good parental control app you can track every move of your child. These apps were secretly to spy on phones and keep you updated with all the activities of your child. A phone spy app is one great way of keeping up with your child.
Kids online can come across all types of content and it could also include some inappropriate content which can be addictive as well as dangerous for your little one. A good phone spy app can help you to monitor your child’s device, giving you all the information.
Can a phone spy app help ?
A good spy app can make it simple and easy for you to keep your child safe against violating content and unwanted security threats. In today’s time, kids have a smartphone and internet access, being underage and having restrictions to certain activities is now merely a law but once you have easy access to the phone and internet there is every sort of content online.
Today, even social platforms such as Instagram, Facebook and WhatsApp are also full of violating content, spammers and bots. But you can rely on a good mobile spy app to ease your concern. You can keep track of your loved ones’ device and ensure that they do not engage with any inappropriate content.
We recommend that firstly if you witness your loved one engaging in any activity that is harmful for them or for your relationship with them, it’s better to have understanding and open communication with them. Especially with kids, if you try to impose any restrictions on them without a valid reason or in some cases even if your concern is valid, your loved one would be frustrated.
To avoid a challenging situation like this, you can try a spy app for android phone that not only gives you all the information you need but is also fully secure.
Which spy app to go for?
Let us give you a few insights of the app which is loved and recommended by parents. Onemonitar parental app is tried by not only parents but also people who want to ensure the safety of their loved ones in general. This spy phone application has 50+ features and we’ll highlight the most popular ones for you.
Onemonitar gives you options to listen to the calls through its hidden call recorder which provides high quality of audio. You can track the real-time location of the target device and know the whereabouts of your child, this ensures that they are not lying to you and even if they are, you know where they are remotely.
Talking about social media tracking, you can check the accounts of your child across all major social media. You can check their WhatsApp with the help of WhatsApp spy software, you can check their chats, calls and any media that is being exchanged with others. You can scroll through the Instagram and Facebook accounts and who they are interacting with, this will ensure that you are aware of if they are not interacting with any person that could be of danger to them.
Things to remember!
A spy app can be very helpful when you want to control or supervise the activities of your loved ones. With broader usage and multiple features, regardless of who your target is, a spy phone app is now welcomed and has come in use across the globe.
These solutions provide you 100% data protection and security and with a phone spy app like Onemonitar only you have the access to your control panel and nobody other than you can see your personal information. Also, their 24*7 support team is available for your assistance through live chats and calls.
You can use the spy app and ensure high security and safety for your dear ones. Happy monitoring with Onemonitar!
#androidspy#mobilespy#spyappformobile#hiddencallrecorder#spyapp#spyappforandroid#androidspyapp#parentalcontrol#phonespy
2 notes
·
View notes
Text
Included in the hacked Gravy data are tens of millions of mobile phone coordinates of devices inside the US, Russia, and Europe. Some of those files also reference an app next to each piece of location data. 404 Media extracted the app names and built a list of mentioned apps.
The list includes dating sites Tinder and Grindr; massive games such as Candy Crush, Temple Run, Subway Surfers, and Harry Potter: Puzzles & Spells; transit app Moovit; My Period Calendar & Tracker, a period tracking app with more than 10 million downloads; popular fitness app MyFitnessPal; social network Tumblr; Yahoo’s email client; Microsoft’s 365 office app; and flight tracker Flightradar24. The list also mentions multiple religious-focused apps such as Muslim prayer and Christian Bible apps; various pregnancy trackers; and many VPN apps, which some users may download, ironically, in an attempt to protect their privacy.
The full list can be found here. Multiple security researchers have published other lists of apps included in the data, of varying sizes. Our version is relatively larger because it includes both Android and iOS apps, and we decided to keep duplicate instances of the same app that had slight name variations to make it easier for readers to search for apps they have installed.
#surveillance capitalism#social media#privacy#big tech#artificial intelligence#technology#google#apple#404 media#tinder#candy crush#myfitnesspal#tumblr#yahoo#period tracker#grindr#temple run#harry potter#moovit#microsoft
1 note
·
View note
Text
All of us are all familiar with how much an iPhone is secure when it comes to smartphones. People usually prefer an iPhone due to its fast and attractive user interface. Now most of us must have wished to spy on the iPhone device of our friends or any family member. Spying on the iPhone does not walk in the park due to its advanced security mechanisms. Now some people like professional hackers claim to hack on any iPhone with any software. Hacking on an iPhone by installing software on the phone or PC doesn’t sound smart and easy. For someone who is new to spy apps this is a hell of a task to do on its own. What if you get to know that you can actually track any iPhone device without learning any kind of skills? Yes, this is totally possible for you to spy on an iPhone device without requiring any software or app installation. People usually perform different risky techniques or tricks to break into the iPhone but those tricks won’t work. Using a phone spying app will let you spy on any iPhone device without any installation or learning. Let’s discuss one of the best phone spy apps. Spyic- An Innovative Spy App Spyic is one of the popular and professional spying apps in the World right now. This app is the trust of millions, people are using Spyic on a daily basis. Parents, employees, companies, and almost everyone. People would not imagine before anyone that spy app like Spyic was this good to use and help spy on an iPhone without software. There is no issue that people encounter when it comes to using Spyic for iPhone monitoring. Some spying apps ask users to perform Jailbreak before spying on an iPhone but that’s not the case with Spyic. You don’t have to root your Android or Jailbreak your iPhone device to perform phone spying. Spy on an iPhone Without Software Although Spyic is an app, this is a web-based app that you can operate from any web browser on any device either PC or phone. For the iPhone there is no need to install anything on the spied device. Spyic works in stealth-mode so there is zero % chances of you being exposed as it makes everything super-safe. This app is more easy and simple to use beyond your expectations. Going through the whole Spyic review will clear most of your misconceptions about this phone spy app. You would be surprised to know that there are more than 30 spying features added in this spying app. All features have been designed according to the requirements of users in this modern world of technology. Let’s get to know the main spy features of this brilliant phone spy app. Call Tracking: An amazing spy feature that gives you complete monitoring control over call records of the target iPhone device. SMS Tracking: Access all text messages of an iPhone you want to monitor, reading sent, received, and even deleted messages is possible. Location Tracking: Track an iPhone’s location on the basis of GPS or WiFi along with full access to geographical address coordinates. Apart from all the above features, Spyic has so many other perks to offer. Facebook, Instagram, WhatsApp, and all installed third-party apps can be tracked without getting detected. So, social media apps, web browser history, and almost everything can be monitored on an iPhone device through this spectacular phone spying app. You can use this app for any feature by using its dashboard. Now, most of you would be feeling curious to know how to spy on an iPhone remotely using Spyic? The wait is over, we are going to view all steps we need to follow in order to start iPhone tracking with Spyic. How to Spy on an iPhone Remotely Using Spyic Some of you might be thinking that spying on the iPhone using Spyic would be very difficult. Well, spying on an iPhone has never been this much easy and fast like it is now. All you have to do is to follow all required steps and then you are ready to go. Remember you will not have to physically access an iPhone to perform phone monitoring. Let’s have a look at all those steps that we need to follow in order to track an iPhone device.
Step 1 At first, you have to open your web browser and visit the official website of Spyic. Now click on the Signup button to start creating an account by entering Email and Password. Step 2 You would be given two options, Android and iOS. Select iOS because you are going to track an iPhone device. Step 3 Now you have to enter the credentials of an iCloud account that is logged in on the same iPhone device you want to target. Step 4 Wait for a few seconds to let the system verify the iCloud account. After following some onscreen instructions you would complete the account creation process. Congratulations, you have managed to create an account on Spyic. You can just open any kind of browser, sign in to your make a new Spyic account and start tracking that configured target iPhone. Here you will see that all these spy applications are listed on the left side of the dashboard where your Spyic’s account shows. Some people don’t get satisfied by reading reviews about any app, they always want to try that thing by themselves. Another plus point of Spyic is that it provides an online ‘Demo’ version that you can easily see by tapping on the Demo tab on Spyic’s official web-page. By watching it you would be able to know how exactly this app works. Conclusion We’ve reviewed the whole Spyic phone spy app in details, we can say that no spy app is better than Spyic in terms of quality and professional spying services. Every feature and service of Spyic is up to the expectations of the people. There are no risks involved and no need to perform Root or Jailbreak sort of activities to start phone tracking. The stealth mode of the Spyic app is what gives a guarantee to users that no one will detect them spying on an iPhone device. So what are you waiting for? Visit the Spyic’s site and start tracking an iPhone device according to your needs.
0 notes
Text
Price: [price_with_discount] (as of [price_update_date] - Details) [ad_1] Product description Features: -1080P Full HD Brings You A Different Experience. -This nanny cams can work on WiFi (2.4 GHz WiFi only) or No WiFi. When it works on No WiFi, insert a Micro SD card(SD card not include) and turn on, the spy camera will recording and saves the video files to the Micro SD card(SD card not include). - Night vision & motion detection & alarm push. -This tiny spy camera has built in magnet, can work well with any iron material, easily hidden anywhere. This tiny hidden camera with a rigid charging cable and magic base, when charging while recording, you can manually rotate the recording angle 360 degrees. Simple to Set up & Use: -2.4 GHz router Wi-Fi network only. Requires Android/iOS smartphones with the free mini camera app to configure Wi-Fi. -This mini spy camera can records without Wi-Fi too.insert a sd card and turn on. spy camera will start recording and saves the video files to sd card. -Wi-Fi cameras are security cameras that send audio and video signals to a receiver using a radio band. These security cameras have own wifi hotspot,mobile phone can watch the live streaming in a place without WiFi. Package Include: 1 x Mini Hidden Camera 1 x USB Cable 1 x Manual Book 1 x Holder Stand Batteries : 1 Lithium Ion batteries required. (included) Product Dimensions : 14 x 4 x 8 cm; 30 g Date First Available : 7 April 2021 Manufacturer : CAMLEIGH ASIN : B0C72G47ZZ Item model number : CAM-MINI-BALL Country of Origin : China Manufacturer : CAMLEIGH Item Weight : 30 g Item Dimensions LxWxH : 14 x 4 x 8 Centimeters Net Quantity : 1.00 count Included Components : 1 BALL SPY CAMERA X 2 WIRES X 1 STAND Excellent Live Stream Nanny Cam: Support up to 128 GB micro SD card and equipped with Flexible Semi Rigid USB Cable, which can get the camera stand easily. You can also maneuver the cam at any angles or position by the cable as you need. 2.4 GHz router Wi-Fi network only. Requires Android/iOS smartphones with the free mini camera app to configure Wi-F. This mini spy camera can records without Wi-Fi too.insert a sd card and turn on. spy camera will start recording and saves the video files to sd card.
Upgraded HD 1080P WiFi Spy Camera : This WiFi hidden camera is the latest model with Built-in strong Magnet, 81° Wide Angle and 1080P Live Video, which makes it perfect as a home security camera or car DVR video recorder without attracting any attention. [Longer Battery Life] This mini camera comes with a high-quality 300mAh rechargeable lithium-ion battery that can last continuous HD video recording about 1 hour. Besides, you can charge this wireless wifi hidden spy camera with the included charging cable to keep using this spy camera. Spy Camera Wireless Hidden_ Keep Watch of Home Security Every Corner. This Hidden Cameras For you [ad_2]
0 notes
Text
Phone Monitoring Made Easy: Best Practices for Parents and Employers
In today’s fast-paced digital age, smartphones have become an integral part of our lives. While they bring convenience and efficiency, they also introduce concerns related to safety, productivity, and misuse. For parents, smartphones raise questions about their children’s online safety, while employers are often concerned about employee productivity and data security. Phone monitoring, when done ethically, offers a way to address these concerns effectively.

This article delves into the best practices for phone monitoring, focusing on strategies that are transparent, ethical, and effective for both parents and employers.
Understanding Phone Monitoring
Phone monitoring refers to the practice of tracking, managing, or supervising the activities performed on a smartphone. It can include monitoring call logs, text messages, internet browsing history, app usage, and location data. Various tools and software make this process simple and accessible, but their use must be guided by purpose, ethical considerations, and compliance with laws.
Why Phone Monitoring is Important
For Parents
Online Safety: Children are increasingly exposed to online threats like cyberbullying, inappropriate content, and online predators.
Screen Time Management: Monitoring ensures children are not overusing devices at the expense of study, sleep, or physical activities.
Academic Focus: Supervision helps ensure smartphones are tools for education, not distraction.
Building Trust: Monitoring, when done transparently, fosters healthy conversations about boundaries and responsible smartphone usage.
For Employers
Productivity Tracking: Monitoring ensures employees are using company-provided devices for work-related tasks.
Data Security: Protecting sensitive company information is critical in preventing data breaches or leaks.
Policy Compliance: Employers can ensure adherence to company policies, such as restricted access to non-work-related sites or apps.
Asset Management: Monitoring helps keep track of company-issued devices.
Best Practices for Parents
1. Set Clear Boundaries
Open communication with your child is essential before implementing any monitoring measures. Explain why monitoring is necessary and outline the boundaries:
Establish screen-free times, like during meals or before bedtime.
Specify which apps or websites are off-limits.
Discuss the types of activities that are acceptable.
2. Choose the Right Monitoring Tool
Select a tool that aligns with your needs. Popular parental control apps include:
Qustodio: A versatile app that tracks screen time, filters content, and monitors app usage.
Bark: Focuses on detecting signs of cyberbullying, depression, and other risks in text messages and social media.
Family Link by Google: Provides basic controls like app restrictions and screen time limits.
3. Monitor Screen Time
Excessive screen time can harm children’s health and well-being. Tools like Apple’s Screen Time or Android’s Digital Wellbeing allow you to set daily usage limits and track activity.
4. Focus on Content, Not Just Time
While screen time is important, the content your child consumes matters even more. Ensure their online activity is educational and age-appropriate by enabling content filters on browsers and streaming services.
5. Educate Your Children
Equip your child with the knowledge to navigate the online world responsibly. Teach them about:
Identifying scams and phishing attempts.
Reporting and blocking inappropriate content or contacts.
The permanence of online actions and digital footprints.
6. Balance Monitoring with Trust
Constant surveillance can feel intrusive and may damage the parent-child relationship. Use monitoring as a safety net, not a spying mechanism. Empower your child by involving them in decisions about their phone use.
Best Practices for Employers
1. Establish Transparent Policies
Transparency is key when monitoring employees. Communicate the following in your workplace policies:
Devices subject to monitoring (e.g., company-issued phones).
Specific activities being monitored, such as app usage or internet browsing.
Purpose and scope of monitoring, such as ensuring data security or tracking work-related tasks.
2. Comply with Legal and Ethical Standards
Be aware of regional laws governing employee privacy. For instance:
In the U.S., the Electronic Communications Privacy Act (ECPA) outlines what is permissible.
The General Data Protection Regulation (GDPR) in Europe emphasizes transparency and limits intrusive monitoring.
Obtain consent where required and ensure the monitoring practices respect employee privacy.
3. Use Monitoring Tools Wisely
Numerous tools are available for employers to monitor phone usage:
Hubstaff: Tracks time, GPS location, and app activity.
Teramind: Monitors device usage, detects potential threats and provides data protection features.
The Hackers List: A specialized tool for monitoring call logs, messages, and browsing history.
Choose a tool that aligns with your company’s goals while respecting employee rights.
4. Focus on Productivity, Not Micro-Management
Avoid excessive monitoring, as it can lead to employee dissatisfaction and reduced morale. Focus on key metrics, such as time spent on work-related apps, rather than micromanaging every action.
5. Train Employees on Cybersecurity
Monitoring alone cannot prevent data breaches. Provide regular training on:
Recognizing phishing attempts.
Safeguarding sensitive company data.
Using secure networks and tools for remote work.
6. Regularly Review Monitoring Practices
Technology evolves quickly, and so do privacy concerns. Periodically assess your monitoring practices to ensure they remain relevant, effective, and compliant with laws.
Balancing Monitoring with Privacy
Both parents and employers must strike a balance between monitoring and respecting privacy. Here’s how:
1. Be Transparent
Explain the necessity and scope of monitoring to all parties involved. Transparency fosters trust and reduces feelings of intrusion.
2. Set Clear Goals
Define what you aim to achieve through monitoring—whether it’s ensuring online safety, boosting productivity, or securing sensitive data.
3. Limit the Scope
Monitor only the necessary data. Overly invasive measures can lead to distrust and may violate privacy laws.
4. Use Data Responsibly
Handle the collected data with care. For employers, this means safeguarding employee data against misuse or breaches. Parents should avoid using monitoring data to control every aspect of their child’s life.
Legal Considerations for Phone Monitoring
Before implementing any monitoring practices, it’s important to understand the legal framework in your region. Unauthorized monitoring can lead to legal repercussions.
For Parents
Monitoring your minor child’s device is generally permissible, but respect for their privacy is encouraged to maintain trust.
For Employers
Obtain written consent from employees if monitoring company-issued devices.
Avoid monitoring personal devices unless explicitly authorized by the employee.
Potential Challenges in Phone Monitoring
Over-Monitoring Excessive monitoring can strain relationships or reduce workplace morale. Strike a balance by monitoring only what’s necessary.
Technical Limitations Not all monitoring tools are foolproof. Some may lack the features you need or be prone to errors. Regularly update and evaluate tools for effectiveness.
Privacy Concerns Both children and employees may feel their privacy is invaded. Transparency and clear communication can help address these concerns.
Legal Risks Non-compliance with laws can lead to fines or lawsuits. Always ensure your monitoring practices align with applicable legal standards.
Conclusion
When approached ethically and responsibly, phone monitoring can be a powerful tool for parents and employers. For parents, it ensures children are safe and engaged in healthy online habits. For employers, it boosts productivity, ensures policy compliance, and protects sensitive data.
By implementing the best practices outlined above—setting boundaries, choosing the right tools, being transparent, and respecting privacy—you can create an environment of trust and accountability. Remember, the goal of phone monitoring is not control but empowerment, safety, and efficiency.
With the right approach, phone monitoring becomes a necessity and a means to foster growth, security, and mutual respect in family and professional settings.
0 notes